CYBERSECURITY RESEARCHER
[ System Hardening | Linux Development | Blue Team Operations ]
Strengthening systems, reducing attack surfaces, and engineering Linux distributions built for security. Welcome to my digital fortress.
[ System Hardening | Linux Development | Blue Team Operations ]
Strengthening systems, reducing attack surfaces, and engineering Linux distributions built for security. Welcome to my digital fortress.
I'm Emir, a cybersecurity professional with expertise in system administration and Blue Team operations. I specialize in securing Linux environments, implementing system hardening, and optimizing operational resilience.
My work focuses on minimizing attack surfaces, enforcing strong security defaults, and designing reliable, privacy-conscious solutions.
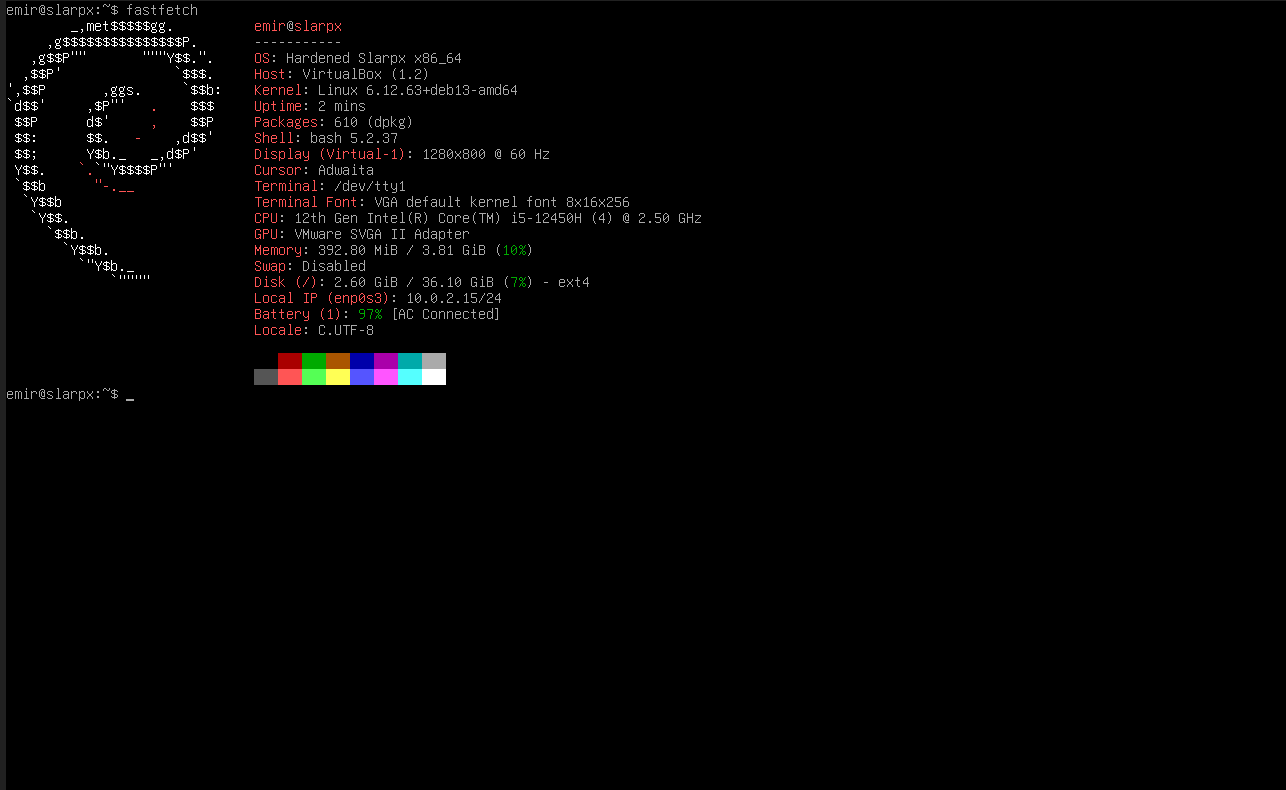

Hardened Slarpx is a Debian-based Linux distribution built with a strict security-first approach. It uses a multi-layered defense model with aggressive mitigations and extensive kernel-level hardening. Includes custom security modules: Poison and Xennytsu. Focuses on active intervention, sabotage, and destruction of attack paths.


Linux Engineer Toolkit (LengToolkit) Live is a specialized, recovery-oriented Linux distribution designed for system engineers and IT professionals. Operating exclusively in Live mode, it provides a robust environment to rescue failing systems, recover lost data, and manage disk infrastructures without installation.

Zenclora is a Debian-based desktop Linux distribution optimized for stability and daily use. Zenclora offers simplified package and system management commands to make Linux usage easier; it avoids unnecessary complexity while providing control to the user.


Fishy Linux is a fast and minimal Debian-based Linux distribution. It uses the lightweight and efficient LXQT desktop environment. Fishy Linux comes with broad hardware support and can be installed to disk using Debian Installer.
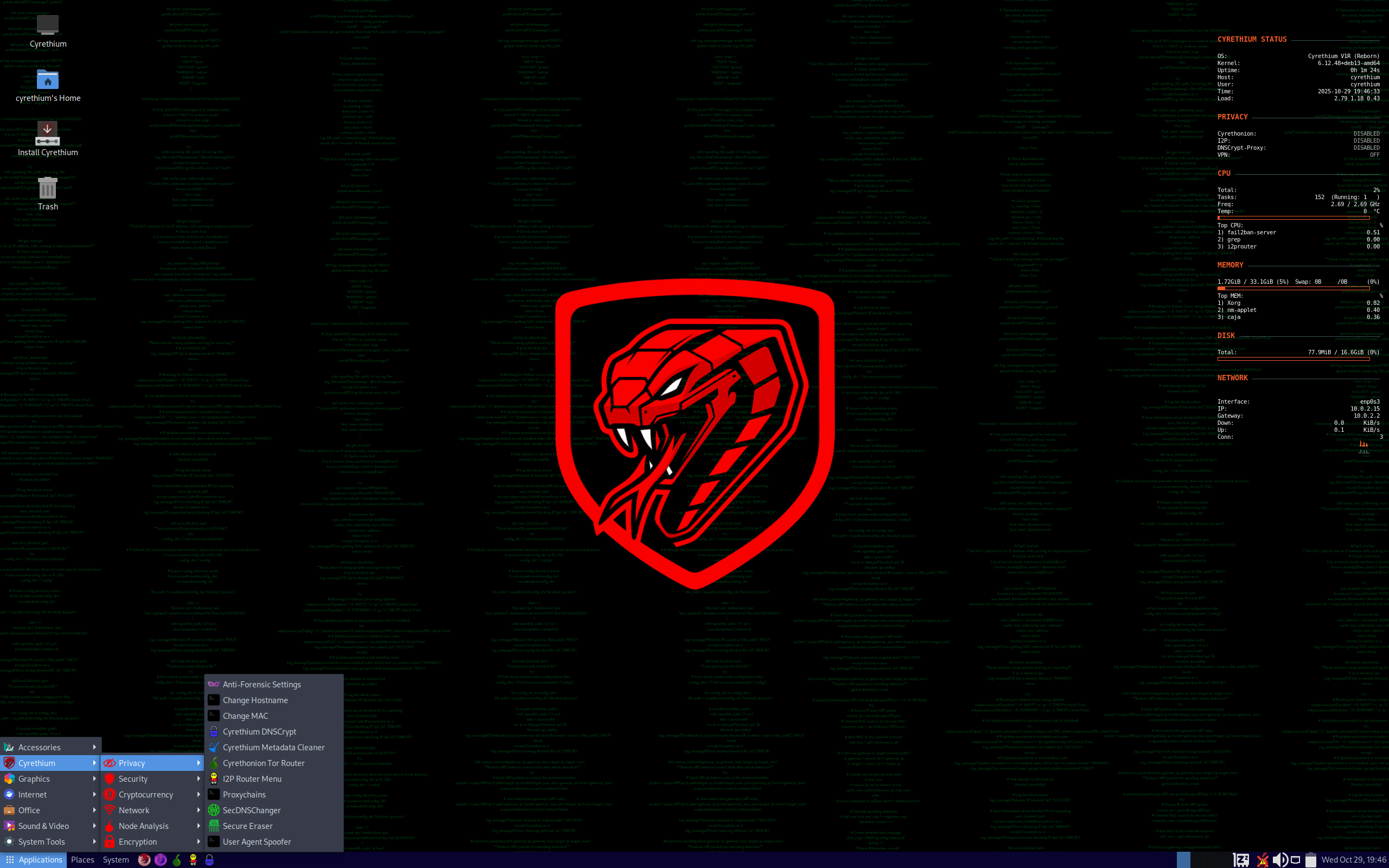

Cyrethium (formerly Securonis Linux, previously known as Portal OS) is a Debian-based Linux distribution focused on privacy and security. Routes all traffic through Tor network. Pre-configured DNSCrypt-Proxy and I2P Router with custom hardened Firefox variants. 4 versions available: 2 core and 2 respins.
Limits application actions using file-based security profiles
Enforces mandatory access control policies for system processes
Containerization and orchestration for scalable deployments
# Establishing secure connection...
$ echo $CONTACT_INFO
Ready to collaborate on security projects
$ cat email.txt
root0emir@protonmail.com